Social engineering attacks are one of the top techniques used against networks today. Why spend days, weeks, or even months trying to penetrate layers of network security when we can just trick a user into running a file that allows us full access to their machine and bypass antivirus, firewalls, and many intrusion detection systems?
This is most commonly used in phishing attacks today, craft an e-mail or create a fake website that tricks user into running , malicious file that creates a backdoor into their system. But as a security expert, how could we test this against our network ? Would such attack work, and how could we defend against it ?
Kali Linux includes one of the popular social engineering attack toolkit available, Devid kennedy’s Social Engineering Toolkit (SET). Devid’s team is very active on SET, there are always new features and attacks being added, More recently several non-social engineering tools have been also added to SET making it a very robust attack tool.
In this post we will take a look at some of the tools included with SET and two of the attacks options, both powershell based attacks.
We can start SET from the Kali Linux main menu :
Kali Linux > Exploitation Tools > Social Engineering Toolkit
Or we can type following command in a terminal :
setoolkit
The Screenshot is following :
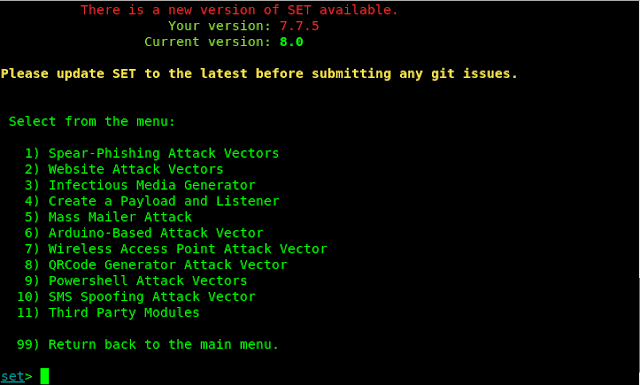
We can see the Social-Engineering Attacks in the top of the menu, so we choose number 1 and hit Enter. Then we will be displayed social engineering options as we can see in the following screenshot:
Here we get all type of social engineering options as following :
- Spear-Phishing Attack Vectors
- Website Attack Vectors
- Infectious Media Generator
- Create a Payload and Generator
- Mass Mailer Attack
- Arduino-Based Attack Vector
- Wireless Access Point Attack Vector
- QRCode Generator Attack Vector
- Powershell Attack Vectors
- SMS Spoofing Attack Vector
- Third Party Modules
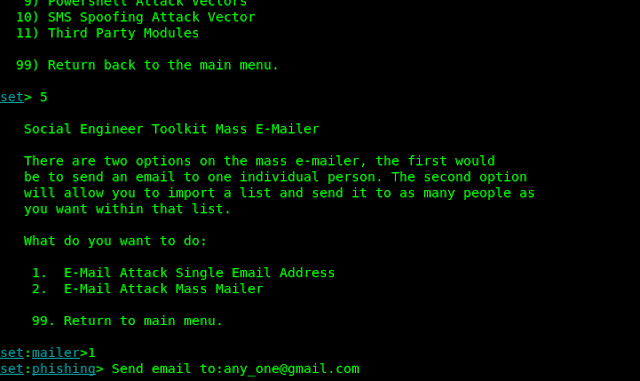
Here in this tutorial we choose options 5. That is Mass Mailer Attack.
Mass Mailer
One way a Social Engineer will attack a network is to send out a flood of e-,ails to company address and see who will respond or run the malicious attachment we sent with it.
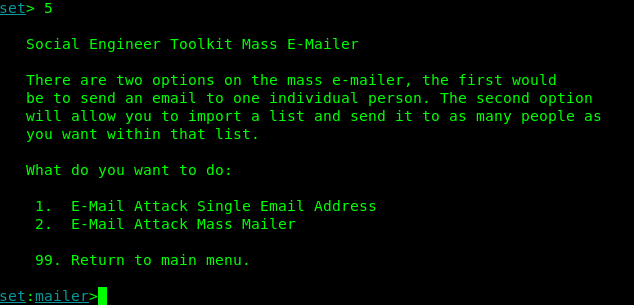
After entering in option 5 in SET we got two options
- E-mail Attack single E-mail Address
- E-mail Attack Mass Mailer
The screenshot is following:
For this example let’s just send one. We press 1 and hit “Enter”.
Then we enter a target e-mail address. See the following screenshot :
For this example, let’s just send one. We press 1 and hit “Enter“.
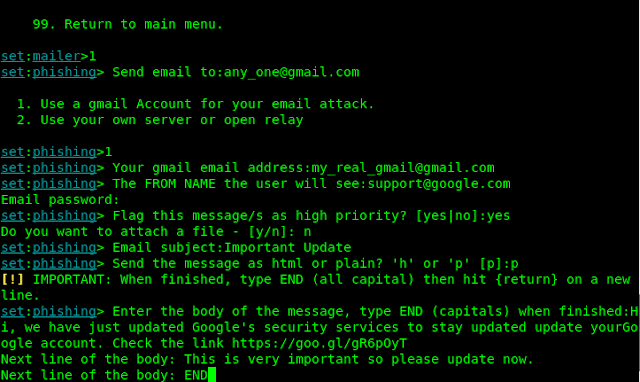
Now we select option 1 to use a Gmail account or another server. For this tutorial we will use a fake Gmail account. The Gmail address and password must be correct.
Then we choose a spoofed name to use for the ‘from’ line of the message. Let’s use “supporrt@google.com” so it look that it’s from Google. Pay special attention to this field, as this where the real social engineering takes place.
Now SET asks for the password of the Gmail account.
Then we press yes at the prompt “Flag this message/s as high priority ?”
We don’t want to attach any malicious file so we choose “no” when prompt “Do you want to attach a file ?”
Next enter an e-mail subject line. What about “Important update”
Enter “p” when prompted to “Send the message as html or plain ?”
Now type-in a fake message, preferably one that will entice our victim to click on a malicious link included or entice them surf to a malicious web page. In actual defense practice this could just be a test webpage that records the IP address of those who were tricked to surf to the page. That way as a security expert we know who in our organization needs to be better educated on the risks of malicious e-mails.
When finished we type “END” in the last line. Just like following screenshot.
Then press “Enter” and SET will send out the e-mail to victim.
The message in above screenshot is obviously a silly fake, but something like this (With a much more believable message ) could be used to test employee’s ability to detect, resist and report phishing attempts.
Java PYInjector Attack
So far we have just sent a fake e-mail that could redirect someone to a bogus site. But if we could make a fake site that offered up a booby script, and if the user allows the script to create shell with the user.
The Java PyInjector attack leverages the anti-virus bypassing capabilities of PowerShell based attacks with a Java application. We will use SET to create a fictitious website that will offer up a booby-trapped Java app, and if user allows the app to run, we get a full remote session to the system.
We will be using a Windows 8 system as the target in the example.
From the SET menu we choose number 1 for Social-Engineering Attacks. Then we choose 2 for Website Attack Vectors. Now we choose number 1 for Java Applet Attack method.
This will create a Java app that has a backdoor shell.
The Metasploit Browser Exploit attacks the client system with Metasploit browser exploits. The Credentials Harvester Attack is pretty slick as it clones an existing website (like Facebook) and then stores any credentials that are entered into it.
TabNabbing works great if the client has a lot of browser window open, it waits a certain time then switches one of the tabs to a page that SET creates. The Web-Jacking attacks uses iFrame replacements to make a malicious link look legit, and finally the Multi-Attack combines several of the above attacks.
Next choose 1 for Web-Templates to have SET create a generic webpage to use, or use option 2 ” Site Cloner ” to allow SET to use an existing website as a template for the attack webpage.
Choose yes/no in NAT/port forwarding. Usually selecting no will be sufficient if using an internal testing lab.
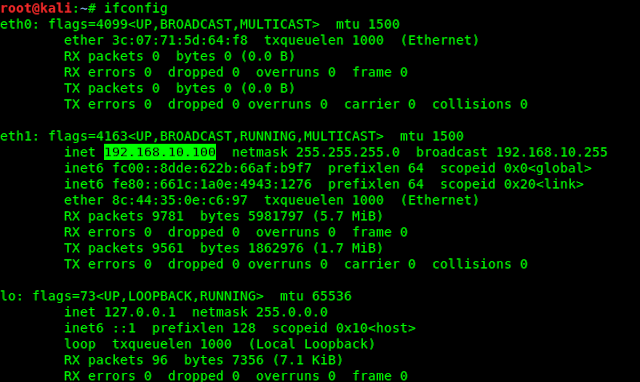
Enter the IP address of our SET machine. We can open another terminal window and type following command for the IP address:
ifconfig
The IP address is in the following screenshot:
Now select a template choose 1 “Java Reuqired“.
Then we pick a payload we want delivered, we usually choose 14 “ShellCodeExes Alphanum Shellcode” (This is an interesting as it runs from memory, never touching the hard drive, this effectively by-passing some anti-virus programs ) or 15 “PYInjector Shellcode“. For now let’s go ahead and use option 15, “PYInjector Shellcode Injection“default port 443.
Next choose a payload to inject. let’s pick the first option “Windows Meterpreter Reverse TCP“.
Now SET is all ready to go and does several things. It creates and encrypts the Powershell injection code, creates website, loads metasploit and starts a service looking for people to connect. When done our screen will look like following screenshot:
Now we need to trick victim that he clicks on our malicious link. Here we have hosted the site in our local host so the link will be the IP address of our Kali Linux system and victim should be in our same network. Victim’s browser want’s to run our malicious Java applet in popup. If he click on “Run”, our meterpreter session will started and we can do anything on victim’s PC.
To do this on WAN (on Internet, not only in local network) Read this tutorial Easy Port Forwarding using SSH .
The Social Engineering Toolkit is truly a robust and feature rich tool for any corporate security testing team.
Spend some time with SET and check out numerous options it offers for attacking a target system. You can use SET to create malicious CD/DVD and USB media (for creating malicious media and leaving them in corporate parking lots, etc), a slew of arduino based attacks, Microsoft SQL Brute Forcer, Wireless Access Point attack, a Mass Mailer, QR code Attack and a bunch of website social engineering attacks that we did not cover yet. Comment below which tutorial should comes next.