Kali Linux users need to do penetration testing jobs and networking always took a big space in penetration testing syllabus. A static IP address will always help us. We don’t need to check for our IP address again and again, and our networking structure will be stable.
There are many ways to configure a static IP address:
- Configure static IP in router settings.
- Configure static IP in the Network Manager in our Kali Linux.
- Configure static IP in command line.
- Configure an External static IP.
Configure static IP in router settings
We can bind a fixed/static IP address with our mac address (unique & fixed hardware address for every device) in our router’s setting.
The process may vary in different models of the router, but the technique will be the same. Usually these function is located
LAN Settings (Local Network) > DHCP Server > List of assigned IP addresses bypassing DHCP.
The specific steps for binding the MAC address to the IP address in the router settings depend on the router model. Therefore, if we have any trouble or we can not find the desired setting in our router, then we should check its manuals.
If we configured static IP router settings, then the actions do not depend on the device to which we want to assign a static IP address, since all the configuration is performed in the router. Also, if we reset all the settings on our device the IP address remains static.
For example if we reinstall our Operating System on our computer or hard reset our phone , then our router will assign the same static IP to our that device, because we have binded the IP address with the MAC address (which is always static).
Note: This method is not applicable for virtual machines, even if a network connection of the Bridge type is used. (But why ? Guess the simple reason and answer us in the comment section).
Configuring Static IP Address in Network Manager
In Linux with Graphical User Interface (GUI) we can configure a static IP in the Wired Settings.
Here we can configure a static IP for our wired connection and also for wireless connection. For example we set a static IP address for one of our wireless networks. Process for configuring the wired will be the same.
First we open the network manager from the application menu Settings -> Advanced Network Manager or we can search for it. Shown in the screenshot:
After opening the Network Manager we got a window like following:
Here we need to choose our WiFi router which one we want to fix our IP address. So we choose our home network by double clicking over it.
Now we got a new window like following:
Here we need to navigate to the IPV4 Settings tab and we got this:
Here we need to change the method to manual. Then on “Additional static addresses” field we click on Add to add a static IP address.
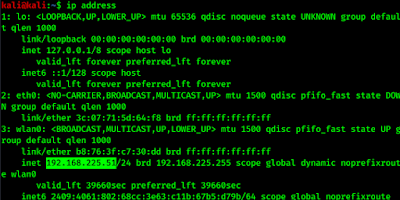
Here we need to enter the desired static IP in the ‘Addresses’ field. Note that it should match our network, for example, if the router (default gateway) has the address 192.168.0.1, then the selected address should be 192.168.0.*. So we need to check our router’s IP address; this is also called default gateway. To check this we need to run following command in our terminal :
In the above screenshot we can see that our router’s IP address is 192.168.225.1 so we choose 192.168.225.100. We think it is easy to remember for us.
Note: We can’t choose 192.168.225.001 because 192.168.225.1 and 192.168.225.001 will be the same in the case of IPV4.
After choosing the address we need to choose the netmask. We should type here 255.255.255.0 because this netmask will be suitable for most of the tasks.
In the Default gateway field we need to enter our router’s IP address in our case this is 192.168.225.1.
We are almost done. Click on apply to save it. Then we must restart our network manager to see the effect otherwise it will be activated from the next boot up of the computer. We simply apply the following command in our terminal to restart our network manager.
Now we check whether our static IP address is configured or not ? We just check for our IP by using following command:
Here we can see that our IP address is changed. This is the process to configure a static IP address in Kali Linux in Network Manager settings. If we need, we can also set the DNS server settings, but this is not mandatory.
Configuring Static IP in command line
We also can configure a static IP address in the command line interface from our terminal. First we need to configure a file “/etc/network/interfaces”. Let we open this file in our favorite text editor by using following command:
Then we add the following lines at the end of the file:
#Static IP address
auto wlan0
iface eth0 inet static
address 192.168.225.100
netmask 255.255.255.0
gateway 192.168.225.1
Here wlan0 is our wireless interface. We can check our interfaces using ip addr command.
The address is our desired static IP address and netmask is 255.255.255.0 will be suitable for most of the tasks, gateway is the IP address of our router. Router’s IP address may vary by its manufacturer.
Then we save and close it by CTRL+X then Y then ‘Enter’ as we save our changes in nano editor.
For the changes to take effect, reboot our system by using following command:
After reboot we check for the IP address using ip addr command, the screenshot of the command is following:
As we can see in the above screenshot, the network interface is really assigned to required IP and now it will be saved after each reboot.
This is how we can set a local static IP in Kali Linux or any other Debian based Linux distro.
Configure an External static IP
Well, this isn’t controlled from our side. It totally depends on our Internet Service Provider (ISP). We can ask them for a static external IP address (May they took some extra charge for this).
There is another way to convert our dynamic IP to a static IP, the service called NO-IP. This service provides a hostname for us and we also need to install a client software in our system. The client will check for external IP provided by ISP. Whenever the IP changes it updates it with the hostname and we can use the hostname as our static IP address. We can follow this tutorial to install No-IP.
Liked our genuine and tested tutorials ? Then make sure to visit our website regularly. For any help comment down we always replay. Don’t forget to follow us on Twitter and Medium, we update small news and our new articles there.