As penetration tester we encounter with web-servers a lot. Before doing any attacks we first study how it is? and gather various information on it which is called “information gathering” sometime it called “reconnaissance” or “recon” in short in cyber security term.
To do recon we need various tools and websites. We go there and put our target domain or IP and try to gather info about it. But on our this article we are going to learn how we can easily gather information from one tool. This tool is called Findomain. Now this tool will use services we need by it’s own and show us the results. It’s also capable of subdomain monitoring, alerts via Discord, Slack and Telegram, multiple
API Keys. Lets install Findomain on our Kali Linux system and try to learn about it’s use.
Installing Findomain on Kali Linux
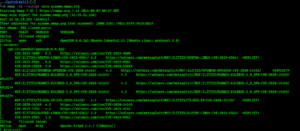
Nah, we should not make a headline about it, it’s very simple, but we have to do it for better Search Engine Optimization. We just need to run following command to install Findomain on our updated Kali Linux system.
After applying the above command it will prompt for password of current user. Then the installation of findomain will start on our Kali Linux, as we can see in the following screenshot:
The installation process will not take a minute, depending on our internet speed and system configuration.
Using Findomain on Kali Linux
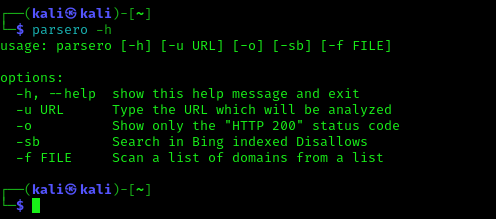
Before run findomain against any target as always we will take a look on it’s options by running following command:
We can see the output in the following screenshot:
Now we can set various platfrom’s API on findomain. For an example we are going to demonstrate how we can set SecurityTrails API on this tool. First we open SecurityTrails website.
Then we need to click on “Sign Up Free” on the top right corner. Then we have the “SignUp” page as we can see in the following:
Here we can upload our details and sign up here. They will verify our email so we need to use original email or temp mail. After the mail verification is complete we can see our accounts page as following:
Here we need to click on the “API” section. Then “API Keys”, and we get our API Key, as shown in the following screenshot (Our API Key is hidden due to security reasons):
Here one thing to remember on the basic Free plan of SecurityTrails we can use the API keys 50 times a month.
Okey, Now we need to set it on our Findomain, we just have to copy our SecurityTrails API key and run the following command on our terminal:
We can see the above thing on the following screenshot:
Just like this we can add various API’s on our Findomain tool. Here we can know more about it.
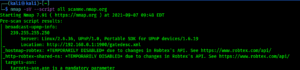
Now run Findomain against a target for an example here we are taking Google (hope they will not mind) and run the following command:
The results are as following screenshot:
There are many type of uses this tools offers, some of them are as following:
1. Make a search of subdomains and print the info in the screen:
2. Make a search of subdomains and export the data to a output file (the output file name in it case is example.com.txt):
3. Make a search of subdomains and export the data to a custom output file name:
4. Make a search of only resolvable subdomains:
5. Make a search of only resolvable subdomains, exporting the data to a custom output file.
6. Search subdomains from a list of domains passed using a file (we need to put a domain in every line into the file):
7. Search subdomains from a list of domains passed using a file (we need to put a domain in every line into the file) and save all the resolved domains into a custom file name:
8. Query the Findomain database created with Subdomains Monitoring.
9. Query the Findomain database created with Subdomains Monitoring and save results to a custom filename.
10. Import subdomains from several files and work with them in the Subdomains Monitoring process:
Findomain notifications on Telegram/Discord/Slack
Findomain was one of the first tools to use a relational database for tracking subdomains. It can manage millions or even trillions of subdomains, as well as thousands of them at once.
First, we need to choose how we want to receive notifications. The options include Discord, Slack, or Telegram. Here, in the official documentations we can easily learn how to set it up for Discord, Slack and Telegram webhook.
There are some of the uses. We can know about more uses on Findomain’s GitHub page.
This is how we can install and run Findomain on our Kali Linux, which is the fastest and complete solution for domain recognition. Supports
screenshoting, port scan, HTTP check, data import from other tools,
subdomain monitoring, alerts via Discord, Slack and Telegram, multiple
API Keys for sources and much more.
Enjoy our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group & Whatsapp Channel. We are striving to build a community for Linux and cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.