Warning:- This article is for research and educational purposes only. we are not responsible for anything you do or damage you cause from this article. We strongly advise to use against networks that you have permission or you have owned. For demonstration we are going to use our own network.
Previously we have discussed about various WiFi penetration testing methods. Now, in this ultimate guide, we are going to discuss the easiest tool to test the security of a WiFi network using our Kali Linux system. Before starting this article we need to know that our normal computer or laptop’s WiFi usually not capable to crack WiFi networks. They normally don’t support monitor mode and packet injection. We need a capable WiFi adapter to do so. We have a list of capable WiFi adapter for monitor mode and packet injection.
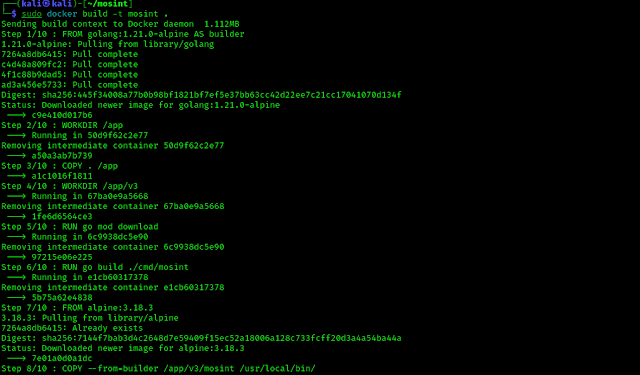
Let’s start, We are going to use a tool named “AngryOxide“. AngryOxide is a command line based tool written on Rust. As of now, it is not included with Kali Linux, so we need to install it from its GitHub repository.
Installing AngryOxide on Kali Linux
First, we start by installing Cargo on our Kali Linux system, as AngryOxide requires Cargo to run. Cargo is Rust’s build system and package manager. We can easily install it via using following simple command on our updated Kali Linux Terminal:
sudo apt install cargo -y
This can take some time to install it depending on our internet speed and system configuration. In the following screenshot we can see the process.
Now we are going to clone AngryOxide’s repository on our Kali Linux system by using following command.
git clone https://github.com/Ragnt/AngryOxide
After the cloning process is complete, we can navigate to the directory and view the files using the cd AngryOxide && ls command [Learn how to use Linux Terminal commands and bash scripting]. We can see the output of above commands from the following screenshot:
Now we can compile it by using following command:
make
We can see the process of above command in the following screenshot:
It may take some time depending on our system performance and internet speed. After finishing this we are gonna install this by using following command.
sudo make install
The following screenshot shows the installation process.
Now we can run this tool from anywhere on our computer. Suppose we need output on our Desktop then we just need to open our Terminal on our Desktop location. To do that we need to run following command:
cd ~/Desktop
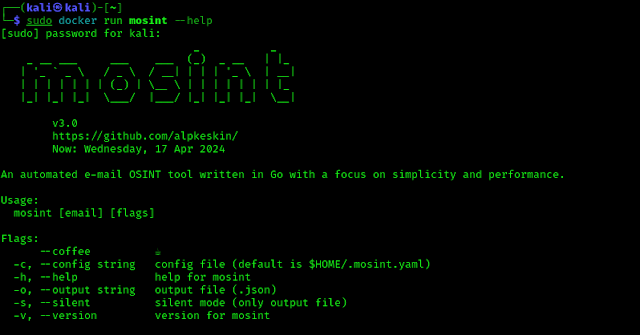
Now we can easily run this tool. Let first we run it check the help options of this AngryOxide tool by using following command:
angryoxide -h
In the following screenshot we can see the help options (menu) of AngryOxide tool.
WiFi Testing Options of AngryOxide
We are going to use these options to crack (better read security test) to any Wireless Network near by. Before that let we understand the working by using the options we got. In following list we are going to break down these options.
- Interface (-i, –interface): This is like choosing which WiFi card or adapter we want to use for testing.
- Channel (-c, –channel): We can think of WiFi channels like different radio stations. This option lets you choose specific channels to scan. If you don’t specify any, it will automatically scan commonly used channels 1, 6, and 11.
- Band (-b, –band): WiFi can operate on different frequency bands like 2.4GHz or 5GHz. This option lets you specify which band or frequency range to scan.
- Output Filename (-o, –output): This is where you specify the name of the file where the results of the test will be saved.
- Target Entry (-t, –target-entry): Here, we can specify a particular WiFi network (identified by MAC address or SSID) that we want to target for testing. If we don’t specify any, AngryOxide will test all networks it finds.
- Whitelist Entry (-w, –whitelist-entry): This is for specifying networks that we don’t want to attack. It’s like commanding AngryOxide, “Leave these networks alone.”
- Attack Rate (-r, –rate): Adjusts how aggressively the tool attacks networks.
- Combine (–combine): Combines output files into one for easier analysis.
- No active (–noactive): Disable activated Monitor mode of WiFi adapter.
- Autohunt (–autohunt): Automatically scans and focuses on channels where targets are found.
- Auto exit (–autoexit): Tells the tool to stop automatically once it has gathered all the needed data.
- No transmit (–notransmit): Makes the tool passive, meaning it observes without sending any data.
- No deauth (–nodeauth): Disables sending deauthentication frames, which are sometimes used in attacks.
- No tar (–notar): Prevents the tool from packaging the output files into a tar file.
- Disable mouse (–disablemouse): Turns off mouse capture, useful for headless operation (no graphical interface).
- Dwell Time (–dwell): Adjusts the time spent on each channel during scanning.
Running AngryOxide against WiFi
First we can check network interfaces we are using on our system by using following command:
ip a
In the following screenshot, we can see the network interfaces on our Kali Linux system.
 |
| MAC address is hidden due to security & privacy |
In the above screenshot we can see that our computer have only a wlan0 wireless network interface. We are using Kali Linux on our Desktop PC and that is an external WiFi card Alfa AWUS036NEH, if we were using a laptop then we might get two wireless network one for inbuilt wireless card another for external wireless card. in that case we have wlan0 and wlan1 as our network interface.
Now we run AngryOxide tool to set our interface (wlan0) without making any noise on surrounding networks with no deauth and no transmit options. Here we requires root permissions, so our command will be as following.
sudo angryoxide -i wlan0
In the following screenshot we can see that our AngryOxide is running with a very beautiful command line interface and discovered some wireless networks. Here we also can see various options regarding discovered networks. Here we can use our keyboard for navigating things like q to quit, a/d to change tabs, space for pause, w/s to scrool, k for keybinds.
 |
| We have hidden MAC addresses to maintain our privacy. |
Here for an example we have choose a WiFi network named Zero (SSID is the name of the WiFi Network). To select it we need to press down arrow key ⬇. Then we need to press 🇹 button on our keyboard to start attack on it. As we can see in the following screenshot.
We can also see that we have captured 4-Way Handshake. 4-Way Handshake is capturing 4 messages (EAPOL Messages). Basically in normal language to understand this attack process we think like AngryOxide send de-authentication packets to target network (lots of packets on a network) which creates a traffic jam and all connected devices are disconnected due to overload then those connected devices or clients automatically try to connect to the network and send request to connect. Here is the catch in that request it send password also for validation. Password in the sense hash of the password. We capture the request using various applications just we are doing using AngryOxide. This capture process called handshake capturing.
If we press 🇩 on our keyboard two times and go to the “Handshake” tab then we can clearly see that AngryOxide have captured handshakes successfully. Which shown in the following screenshot.
Now our work is done. We can quit this by pressing 🇶 button on our keyboard.
Then AngryOxide will ask for confirming the exit. Here we press 🇾 button to confirm our exit. We had run AngryOxide on our Desktop so after exit we can see a ZIP file on our Desktop. As we can see in the following screenshot.
Now we can easily extract this ZIP file by right click and choosing “Extract Here” option.
It will create a directory (Folder for Windows users) on our Desktop, inside that directory we can see some files.
Cracking WiFi passwords
YOO! Handshake file is captured. Now what? It’s time to crack down this hash into plain text password. To do this we are going to use HashCat tool. Previously we have discussed about Hashcat.
Sometimes we got the handshake (cap/pcap/pcapng) file then we need to convert it to put it on Hashcat for cracking Paswword. But AngryOxide already providing us the Hashcat format (filename.hc22000 format) which saves our some time. Lets crack this using Hashcat.
We need to open a terminal window and run following command:
hashcat <full-path-of-hashfile> <full-path-of-wordlist>
In our case the command will be as following
hashcat /home/kali/Desktop/oxide-2024-05-01_21-14-38/Zero.hc22000 /usr/share/seclists/Passwords/WiFi-WPA/probable-v2-wpa-top447.txt
Here we are using a passwordlist or wordlist which contains top 447 common passwords for WiFi cracking. We can download these kind of wordlists from internet (here we have used seclists, which can be installed on Kali Linux by sudo apt install seclists command).
 |
| Hashcat is trying to crack the password |
If the password isn’t common, then we might not find it. In that case, we need to run a dictionary attack. Which may took several years to crack a tough password depending on our System password (GPU’s are useful in this case).
We intentionally put an easy password for our WiFi to demonstrate this tutorial. But with a large wordlist the chance of cracking the hash increased.
In the following screenshot we can see that password for SSID named Zero is cracked.
This is how we can easily capture WiFi handshake files using AngryOxide and crack WiFi password using Hashcat on Kali Linux system.
Note:- This article is intended solely for educational and research purposes. We hereby absolve ourselves of any responsibility for the consequences of actions taken as a result of the information provided herein. Proceed with caution and understand that unauthorized use of the techniques described within may result in severe legal repercussions. We vehemently advise against employing these methods on networks without explicit permission from the network owner or administrator. For the purpose of demonstration, we will be conducting our experiments exclusively on our own network.
Love our article? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group & Whatsapp Channel. We are striving to build a community for Linux and cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
![🛠️ Hack Smarter! Install DeepSeek AI on Kali Linux in 2 commands! [No GPU]](https://binpur.com/wp-content/uploads/2025/03/DeepSeek-20on-20Kali-20Linux-20Thumbnail.jpg)