Today we are going to learn about recon-ng. Recon-ng is very good tool for web application analysis.
Recon-ng is a fully featured Web-Reconnaissance framework which written in Python3. It gives a powerful environment to it’s users.
Recon-ng have some modules and functions which gives many useful information about the target, like sub-domains, IP, Geo-locations, vulnerabilities etc.
Recon-ng’s look and feel is close to metasploit framework This tool comes pre-installed with Kali Linux.
Let we check how we can use this tool as a basic user. Let we fire up our Kali Linux’s terminal window and apply following command:
Our call will open this framework as shown in following screenshot:
Here we got recon-ng version 5.0.1. We can see in the above screenshot that in this version ‘no modules enabled/installed’.
Let we run help command to see the help options.
We can install modules from the market places. To see all the list of modules we can run following command:
Then we can see all the modules in recon-ng as we can now see in the following screenshot:
Now if we want to install “hackertarget”module then we can search for it’s path using following command:
After applying this command we can see the path of hackertarget as shown following screenshot:
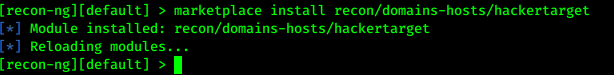
Now in the V5 of recon-ng no modules comes pre-installed so we need to install “hackertarget” module. We can easily do it by applying following command:
So here we used marketplace install and the path of module, that’s it.
This will install “hackertarget” module.
This is how we can install modules in recon-ng V5. But some advanced modules requires api keys to run.
Now we load a module for scan. For an example we choose “hackertarget” and load it by using following command:
Now we can set sources with target, by using following command:
Now we can run by using run command.
Then this module will run on kali.org domain, as we can see in the following screenshot:
We can see after process complete that we got total 49 hosts These hosts are added in the hosts table. We can check by using following command:
The screenshot is following:
We can see hosts in hosts table this is how we can use Recon-ng V5 in Kali Linux.
Follow our blog to get latest tutorial as soon as possible. Follow us on Twitter and Medium.






Leave a Reply